 SAP SNC Component
SAP SNC Component
Component
This component is used to configure SaaS RunMyJobs or Finance Automation environments for SAP SNC connections. This allows you to connect the SaaS central Redwood server to your SAP systems. You configure the spool host on the platform agent-side to retrieve output files.
For on-site RunMyJobs or Finance Automation deployments, see Configuring SNC.
| Name | Description | Availability |
|---|---|---|
| REDWOOD_SAPSNC_Tooling | Maintaining SNC configurations in SaaS environments. | On request. |
Contents of the Component
| Object Type | Name | Description |
|---|---|---|
| Application | REDWOOD.CUS_FCA.REDWOOD.CUS_FCA_SAP.REDWOOD.CUS_FCA_SAP_SNC | SAP SNC Tooling |
| Process Definition | REDWOOD.CUS_FCA_SAP_SNC_Tooling | SAP SNC: Tooling |
| Library | REDWOOD.Custom_Redwood_SAPSNC | Redwood library for SAP SNC |
Introduction
The following is required to be able to activate SNC connections.
| Requirement | Section |
|---|---|
| SNC enabled in Target SAP System(s) | See Initialize SNC in SAP System |
| SNC Certificate(s) of Target SAP Systems(s) | See Extract SNC certificate of SAP System |
| Technical SAP User to be used | See SAP User |
- Administrative privileges on Redwood central Server.
- OS User running spool host.
- SAP Cryptographic library.
For x86_64 GNU/Linux (cloud) and your spool host platform.
Redwood_SAPSNC_Tooling
Provides tooling to upload / download SAP SNC related information.
Parameters
| Name | Description | Documentation | Data Type | Direction | Default Expression | Values |
|---|---|---|---|---|---|---|
| ACTION | Action to perform | String | In | GL=Get Startup logfileUL=Upload zip file with SAP Crypto libraryUC=Upload SAP Target System certificateDC=Download the current SAP Target System certificatesRC=Remove a target SAP certificateRL=Remove SNCDP=Download PSE filePC=Download PSE certificateUP=Upload the PSEUS=Upload cred_v2 | ||
| FORCE | Force pre/post actions | String | In | X | ||
| FILE | Upload File | File | In | |||
| NAME | Name of SAP certificate | String | In |
UL- Once you have prepared a ZIP file according to the procedure outlined below, you upload it.UC- Uploads the certificate for the SAP server so that the server is trusted.DC- Downloads the server certificate to allow you to make sure it is correct.RC- Removes the server certificate; you will have to upload a new certificate or you will not be able to use SNC with the target SAP system as the system will not be trusted.RL- Removes the SAP Crypto library.DP- Downloads the PSE files used for SAP SNC.PC- Downloads the client certificate used for authentication.
important
The process definition does NOT support SAP sar files. You must follow the steps in Upload the SAP Cryptographic Library to the Cloud!
Configure RunMyJobs for SNC
The PSE file can be created automatically or you can provide your own PSE file.
Prerequisites
- SAP Crypto library for x86_64.
- Search for
SAPCRYPTOLIBin Downloads on SAP launchpad.
- Search for
- SAP CAR program for your desktop platform to extract the SAP cryptographic library.
- Search for
SAPCARin Downloads on SAP launchpad.
- Search for
- SNC tooling CAR file from Redwood.
- CAR file needs to be imported.
Upload the SAP Cryptographic Library to the Cloud
- Use
sapcarto extract the SAP Cryptographic library:sapcar -xvf SAPCRYPTOLIBP _<version>-<date>.sar -R <destination_path>. - Zip the files in
<destination_path>, no directories allowed in the ZIP file. - Submit REDWOOD_SAPSNC_Tooling.
- Choose UL – Upload zip file with SAP Crypto library in parameter Action to perform.
- Choose Browse and navigate to the ZIP file containing the libraries.
- Choose Submit.
Upload the SAP Target System certificate
Retrieve the certificate of the SAP and upload it to the cloud environment. See Extract SNC certificate of SAP System for instructions. This needs to be done for each SAP System that is connected using SNC.
- Submit REDWOOD_SAPSNC_Tooling.
- Choose UC – Upload SAP Target System certificate in parameter Action to perform.
- Choose Browse and navigate to the certificate.
- Choose Submit.
important
The RunMyJobs instance needs to be restarted after this step!
The certificate must have a crt extension.
The RunMyJobs / RunMyFinance instance must be restarted for the creation of the PSE file and its certificate.
Download the RunMyJobs Certificate
- Submit REDWOOD_SAPSNC_Tooling.
- Choose PC – Download PSE certificate in parameter Action to perform.
- Choose Submit Summary on the left-hand side.
- Choose Monitor process
<process_id>. - Choose Refresh until the process has completed, the certificate will be available under Files.
Prepare Target SAP for RunMyJobs SNC connection
Start transaction STRUST and double-click SNC SAP Cryptolib. Enter the PSE password. If no password is defined, set one!
Switch to change mode
- Import the RunMyJobs certificate.
- Choose Add to Certificate List save the changes.
Update target SAP System Connect String
Once SNC have been enabled on the SAP system, you can update the SAP system connect string with the additional parameters for SNC. If you have not enabled SNC on the SAP application server, follow the instructions in Initialize SNC in SAP System to do so.
| Parameter | Description | Mandatory |
|---|---|---|
SNC_MODE=1 | Activates SNC for the connection | ✓ |
SNC_PARTNERNAME="p[/krb5]:<name>"SNC_PARTNERNAME="p[/secude]:<name>" | Defines the target SAP systems DN (secude) or Kerberos name (krb5) | ✓ |
SNC_SSO=1 | Enable SSO (default) | - |
SNC_QOP=3 | Defines how secure the connection is 1=Auth only, 3=Integrity, 3=Privacy, 8=Default, 9=Maximum | - |
SNC_MYNAME="p[/krb5]:<name>"SNC_MYNAME="p[/secude]:<name>" | Defines the DN (secude) or Kerberos name (krb5) of the PSE to use | - |
Upload your own PSE file
Use the action UP in the SNC Tooling to upload your own PSE file into the cloud.
- Submit REDWOOD_SAPSNC_Tooling.
- Choose UP – Upload the PSE in parameter Action to perform.
- Choose Browse and navigate to the PSE file.
- Choose Submit.
note
The PSE file should NOT have PIN defined to allow access.
Upload your own cred_v2 file
Use the action US in the SNC Tooling to upload your own cred_v2 file into the cloud.
- Submit REDWOOD_SAPSNC_Tooling.
- Choose US – Upload cred_v2 in parameter Action to perform.
- Choose Browse and navigate to the cred_v2 file.
- Choose Submit.
note
The user redwood should be able to gain access to the PSE.
What SNC commands are executed at instance Startup
When the instance is started, the environment required for SNC is defined.
With this environment set, the following sappsegen commands are executed:
- If no PSE file is found.
gen_pse: PSE file is created with aDN(created from URL).
support_info: Details of the existing PSE.seclogin: Add security for the current user.export_own_cert: Create the certificate for the PSE file.- For each uploaded target SAP certificate.
maintain_pk: Add certificate to PSE.
maintain_pk: List all stored certificates.
The output from the commands is contained in the startup.log which can be downloaded using the SNC Tooling action GL.
Spool Host Platform Agent
The spool host Agent needs environment variables setup and the CryptoLib, PSE / cred_v2 files from your RunMyJobs instance to be able to access the correct SNC information.
note
For SNC on UNIX the UUID daemon must be active. For more information see SAP Note 1391070.
**** Trace file opened at 2023-01-01, 08:45:45 GMT
RFC library: 753, Current working directory /data/redwood/agent, Program: jrfc
Hardware AMD/Intel x86_64 with Linux x86_64, Operating_system: Linux 7.12.13-155.89-default, Kernel_release: 753 patchlevel 99
Hostname: pr1.example.local, IP address: 1.2.3.4, IP address_v6: 64:ff9b::1.2.3.4
ERROR The UUID daemon (uuid) is not active.
Please ask your system administrator to activate
uuid according to SAP note 1391070.
- SAP Crypto software for the target platform.
- Copy to
${InstallDir}/saplibs/.
- Copy to
- SAP NW RFC SDK.
- Copy to
${InstallDir}/saplibs/.
- Copy to
- Directory that will contain the PSE file.
- Create
${InstallDir}/sapsnc/.
- Create
- Environment variables.
- Define in
{InstallDir}/etc/startup/default/environment.SECUDIRpointing to the PSE file directory (${InstallDir}/sapsnc).SNC_LIBpointing tosapcryptolibrary (Linux).
- Define in
SNC_LIB = ${InstallDir}/saplibs/<library>.<library>=sapcrypto.dll(Windows)libsapcrypto.so(linux/UNIX).
note
It is also possible to define the environment variables in the following places:
- Globally in
/etc/profile.d - In the Service at
/etc/system.d/system/<service>.service.d
Setting the environment in the user environment is not sufficient for the spool host.
Download the PSE files
- Submit REDWOOD_SAPSNC_Tooling.
- Choose DP – Download PSE file in parameter Action to perform.
- Choose Submit Summary on the left-hand side.
- Choose Monitor process
<process_id>. - Choose Refresh until the process has completed, the file will be available under Files, unzip its contents into the
${InstallDir}/sapsncdirectory.
Create secure login file
Execute sapgenpse to allow the OS user access to the PSE file.
Windows / Unix:
sapgenpse seclogin-v -p <PSE file> -O <OS User>
Extract SNC certificate of SAP System
To extract the SNC certificate of an SAP system you proceed as follows:
- Start transaction STRUST and double-click SNC SAPCryptolib. Enter the PSE password. If no password is defined, set it!
- Double-click on the owner subject. The certificate is now shown:
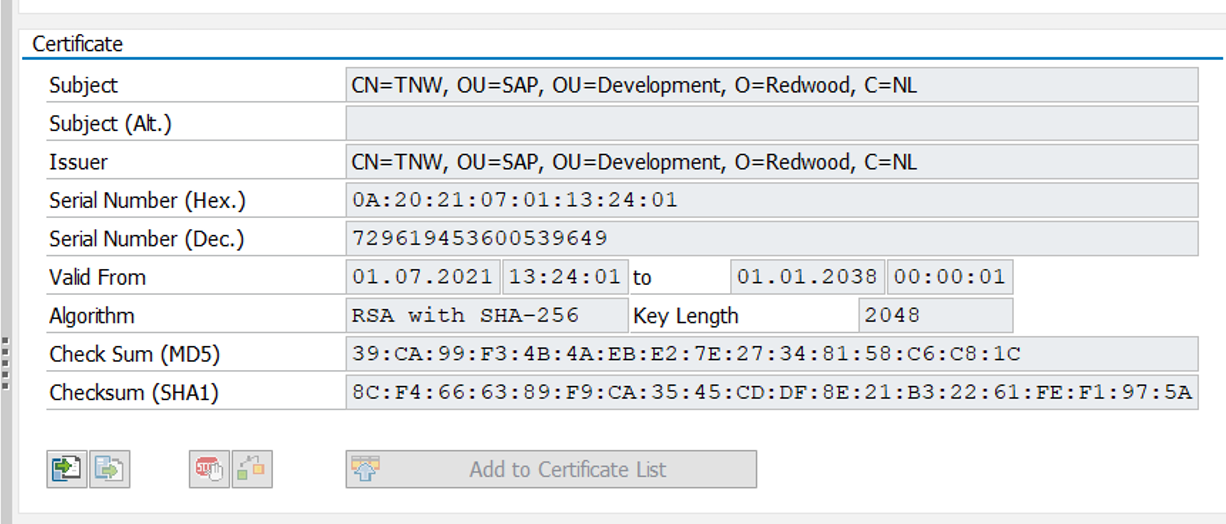
Certificate details.
- Switch to Change mode and export the certificate in Base64 format.
SAP User
In transaction SU01, the SNC tab needs to be filled in. If the tab does not exist, SNC is not activated on the system.
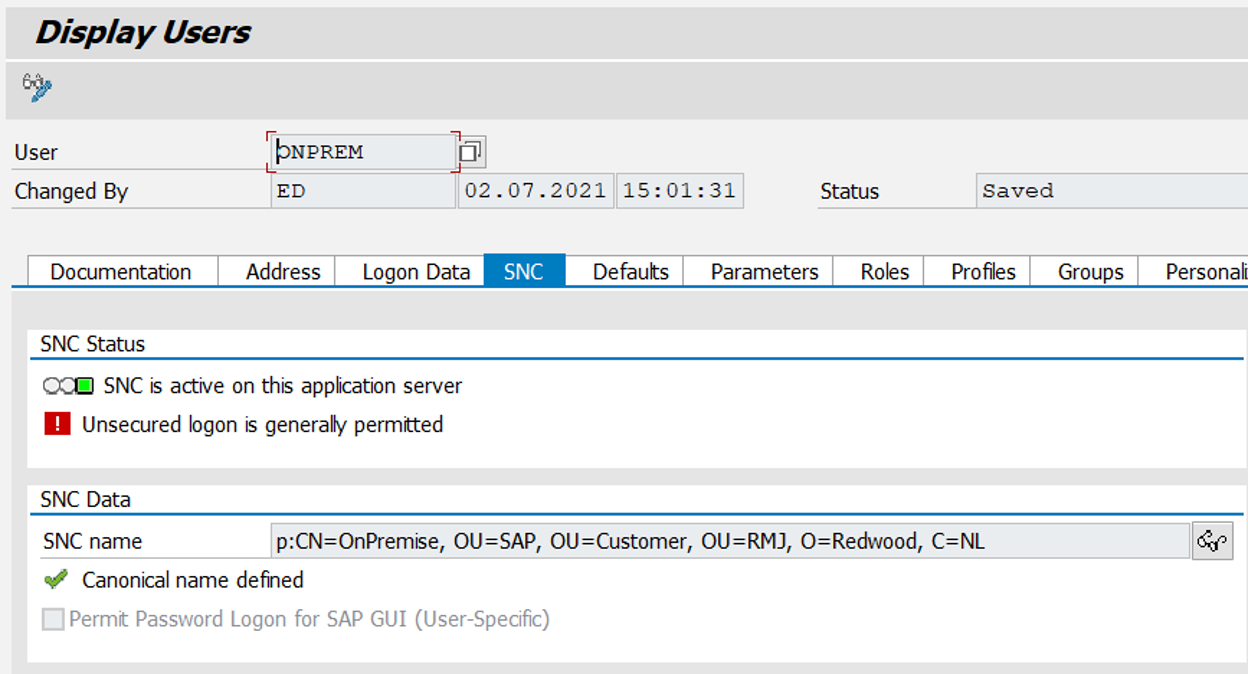
Transaction SU01 displaying a user's SNC settings.
The SNC name uses the syntax <type>[/<tech>]:<name>
where
<type>- is one of the following:p- printable name.s-service@hostname.u- user name.
<tech>- (optional, defaults to active tech) is one of the following:krb5- Kerberos name.secude-X.500name.sapntlm- NTMSSP name (Windows, only).
<name>- Kerberos name such as
jdoe@example.local. - X.500 name such as
CN=John Doe, OU=Administrators, O=Example, C=DE. - NTMSSP name such as
Example\jdoe.
- Kerberos name such as
If the user needs to be connected to more than one PSE, then the additional DNs need to be defined in the table USRACLEXT. See Maintaining SNC Information for Non-Dialog Users for more information.
Initialize SNC in SAP System
Redwood recommends using secude printable names as SNC name, such as p[/secude]:CN=John Doe, OU=Administrators, O=Example, C=DE for example.
Prerequisite
sapcryptolibrary must have been installed on the SAP server.
See Central Note for SNC Client Encryption 2.0 for more information.
Procedure
- Start transaction STRUST and choose Change.
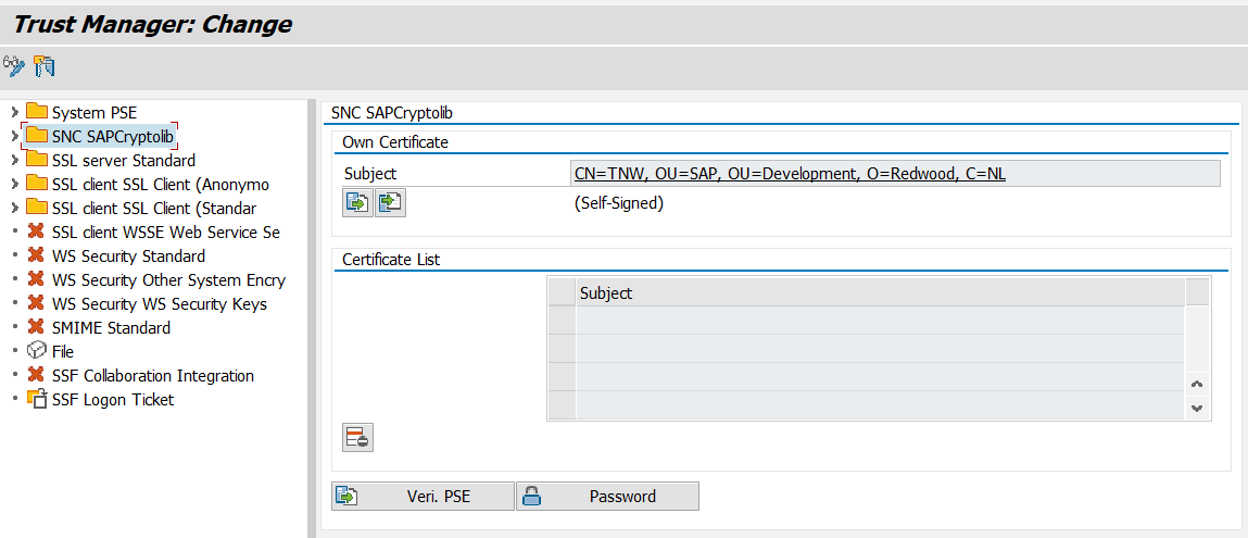
STRUST in Change mode.
- Use context menu "Create" and provide the required information.
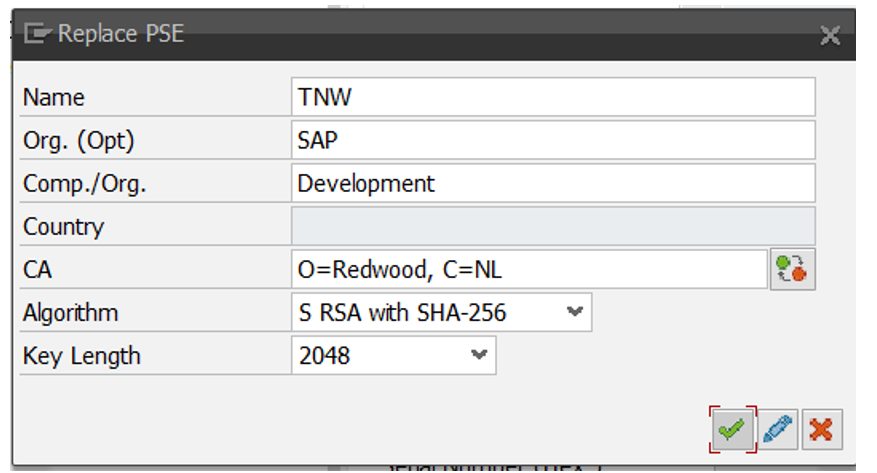
Replace PSE dialog.
- Select the SNC row (double click) and set a password.
SNC requirements
snc/enable= 1
snc/gssapi_lib = $(DIR_EXECUTABLE)\sapcrypto.dll
snc/identity/as= p:CN=TNW, OU=Administrators, O=Example, C=NL
snc/data_protection/max = 3
snc/data_protection/min = 2
snc/data_protection/use = 3
snc/accept_insecure_cpic = 1
snc/accept_insecure_gui = 1
snc/accept_insecure_r3int_rfc= 1
snc/accept_insecure_rfc = 1
snc/permit_insecure_start = 1
Restart the SAP system after these changes.
Testing RFC Connection from Agent
The startrfc executable in the NW RFC SDK can be used to do a connection test.
For SNC it requires a sapnwrfc.ini file containing the connection information.
DEST=PR1
ASHOST=pr1.example.local
SYSNR=00
CLIENT=000
USER=ED
PASSWD=xxx
LANG=EN
NO_COMPRESSION=1
TRACE=2
SNC_MODE=1
SNC_SSO=1
SNC_PARTNERNAME=p/secude:CN=PRD, O=Example, C=SE
startrfc -v
NM RFC Library Version: 750 Patch Level 9
Compiler Version:
180040665 (VVRRPPPPPP. Microsoft C/C++ Compiler)
Startrfc Version: 2023-01-01
note
If you do not get output, then the library cannot be reached (check the path).
startrfc -D PR1 -t -i
SAP System ID: PR1
SAP System Number: 00
Partner Host: pr1.example.local
Own Host: dsk.example.local
Partner System Release: 740
[...]
Checklist for SNC connections
OS Level
| Action | Checked |
|---|---|
| Determine the OS user under which RunMyJobs or spool host is executed | |
Check Environment of OS user for correct SECUDIR, SNC_LIB, SNC_LIB_64 environment settings | |
Check Crypto Library can be used using sapgenpse support_info or sapgenpse cryptinfo | |
Check PSE file is accessible using sapgenpse show -f <pse file> | |
Check SSO credentials are available using sapgenpse seclogin -l -O <os user> | |
Check PSE file contains target SAP system certificates using sapgenpse maintain_pk -l |
Target SAP Level
| Action | Checked |
|---|---|
| Check that the SNC profile parameters are set correctly in RZ10/RZ11 | |
Check that RunMyJobs certificate is stored in STRUST under SNC SAPCryptolib | |
| Check that the RFC User to be used, contains the correct SNC name using SU01 |
RunMyJobs Level
| Action | Checked |
|---|---|
Check the SAP System connect string. Only specify the minimal number of parameters required as this reduces error checking. Example SNC_MYNAME is only required if multiple PSE are defined and used. | |
| If a spool host is used, check that the retrieval of SAP spools is working |
See Also
- SNC Terminology
- Configuring SNC: External Programs → ABAP Platform Using RFC
- Exporting the Server's Certificate Using SAPGENPSE
- Creating the Server's Credentials Using SAPGENPSE
- Maintaining the Server's Certificate List Using SAPGENPSE
cloudTopic
