 Security Overview
Security Overview
This document explains the Redwood Server security architecture and model, including grants, privileges and ranks. It does not cover the ranks available for individual objects, or partitions.
Architecture
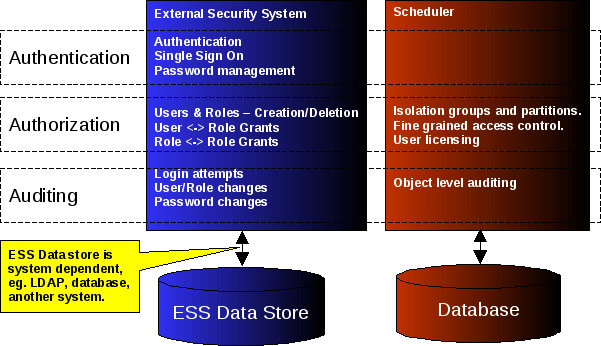
Redwood Server is designed to work with an external security system. The external security system provides authentication (generally using passwords), users & roles, and optionally single sign on.
Security in Redwood Server is split into three main areas:
- Authentication - establishing the identity of the user, often using a username and password.
- Authorization - determining the privileges available to an authenticated user, and preventing unauthorized actions.
- Auditing - tracking what an authenticated user has done.
Authentication
Authentication is handled by the external security system. This includes responsibility for requesting and checking the user's identity (for example, using a username and password), single sign on, and site security policies like password strength requirements, account lockout and similar additional security requirements.
Authorization
Responsibility for authorization is split between the external security system and Redwood Server. The external security system is responsible for users, roles and grants between them. The process for doing so depends on the external security system in use.
Once the external security system has authenticated the user, the username is provided to Redwood Server, which then synchronizes information about the user and their into the system. This information includes:
- The username
- The roles granted to the user.
You can also import users into the system directly from the user interface using the 'Import Users…' action on the context-menu of the Users icon in the Security tab.
note
Information about the user's password is never copied into Redwood Server from the external security system.
The remainder of responsibility for authorization is handled by Redwood Server including:
- Partitions.
- Fine grained access control.
Auditing
Responsibility for auditing is also split. The authentication system is responsible for auditing security actions like:
- Login attempts (including failed logins).
- Changes to users and roles.
- Password changes.
Redwood Server also provides object level auditing. Each time a top level object is modified, the name of the user and the time of the change are set on the object. Rule-based audit history and restore capabilities are provided by the 'Active Auditing' module.
See Also
- External Security Systems
- Lightweight Directory Access Protocol (LDAP)
- Configuring Redwood Server for LDAP Authentication
- Configuring LDAP
- Database Authentication
onsiteTopic
