 On-site Platform Process Servers
On-site Platform Process Servers
Platform process servers are used to perform the following activities:
- Run Operating System processes.
- Watch for file events.
- Observe the system load.
- Act as file servers for OS process files.
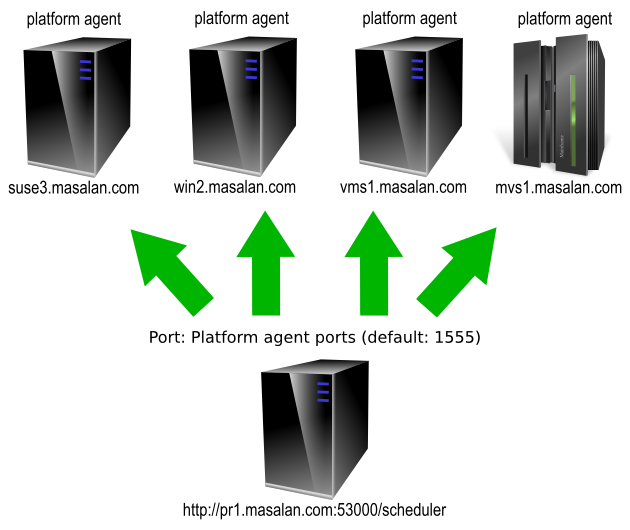
To make this possible a platform agent is installed on the computer system where you wish to run OS processes. The platform agent makes the specific OS system calls required for running OS processes and monitoring the system. The central Redwood Server communicates with the platform agent over the TCP/IP network using the HTTP or HTTPS protocols.
note
When installing a platform agent on an SAP application server, Redwood recommends to name the process server <SID>_<APP_SVR>_PlatformAgent, where <APP_SVR> is the hostname of the application server.
The configuration of a process server that runs OS processes consists of settings in the Repository and the installation and configuration of the platform agent.
The process server is a logical object in the central Redwood Server. It consists of two threads: one is responsible for send messages to the platform agent and the other is responsible for processing messages coming from the platform agent.
The process server is configured using the Process Server Parameters.
Overall settings for all platform agents are configured using the Platform Agent Registry Entries.
The platform agent itself consists of a number of different executables and/or scripts, each playing their own role. How these interact is documented in more detail in the pages below, but in general there are usually at least the following programs:
network-processoris the program that is responsible for communicating with the central Redwood Server.- (UNIX, Microsoft Windows, OpenVMS)
job-processoris the program that is responsible for a single process. When a process starts, an instance of thejob-processorstarts. jtooland derivatives form the System Tools.
For more details see:
- Creating UNIX Process Servers (Advanced)
- User Switching Security Options
- Creating Microsoft Windows process servers (Advanced)
- Creating HP OpenVMS process servers
Platform process servers that schedule workload or use file events require at least one of the following keys:
- ProcessServerService.External.limit - the total number of external process servers (Platform agents, distinct web service endpoints, and SAP connectors).
- ProcessServerService.OS.limit - the total number of platform agent process servers.
Monitoring-only platform process servers on Microsoft Windows and UNIX are free of charge, you may use as many as you like. Monitoring platform agents must have the PlatformAgentService service and are not allowed to have any definition types nor file events.
Support for Networked File Systems
When you want to use Redwood Server in a networked environment there are occasions when you want to use networked file systems in your infrastructure. The term networked file system in this context designates NAS systems, also known as SMB X/NFS/SSHFS file shares; note that SAN file systems, for example mounted via iSCSI, are considered local storage.
This statement outlines the support of platform agents for using networked file systems.
Platform Agents are responsible for the actual execution of processes on an OS level. Platform Agents are not required to run all types of process definitions, notably RedwoodScript, SAP and chains do not require a Platform Agent. When a platform agent is required, it must be installed on the target system that the processes need to be executed on. Platform Agents also have the ability to monitor file systems for changes in directories, and can raise file events upon these changes being noticed.
On Microsoft Windows servers the installation directory and DataRootDirectory must be located on a local file-system.
On UNIX the installation directory can be on a network share. If the DataRootDirectory is on a non-local file-system the following restrictions apply:
- The network file share should support UNIX file modes such as
setuidandsetgidbits, or restrictions may apply to user switching. - The default mechanism for detecting locked files is inoperative. A workaround that uses file age is available.
It is always possible to link files from outside of the DataRootDirectory to processes, if large files need to be stored and managed with the process.
Performance on a network file system will be substantially lower, due to the additional networking overhead when accessing files over the network.
Agent Connection
The central Redwood Server communicates with the platform agent (the network-processor, to be exact) via a TCP connection carrying data in the form of the HTTP protocol. The platform agent is contacted by the scheduler central Java server, and not the other way around. In other words, in terms of the TCP/IP connection the agent is the server and the central Redwood Server is the client. This has the advantage that no incoming TCP ports have to be enabled on the central Redwood Server in order to schedule processes on a machine beyond a firewall.
The default installation procedure also establishes secrets. These secrets are a simple form of key that ensure that a particular platform agent only talks to the Java server that is in possession of the same secret. Message data is also protected by a hash value. The combination of these measures means that it is very hard for an attacker to falsify the communications and act as a Java server.
If, however, you need to protect the content of the data connections as well, you need encryption. Encryption is done using an optional layer that is available only from Redwood directly, as it contains some third party source code. See Secure Agent Connections for more details.
Overriding Process Server Default Values
You can override process server parameter default values globally by setting the following registry entry:
/configuration/ProcessServerParameters/<name>
The <name> is the name of the process server parameter. Note that this registry entry only affects default values; if you add the process server parameter to the process server, then that value will have precedence over the value of this registry entry.
Only the scheduler-isolation-administrator can create/edit these registry entries.
See Also
- Using the Wizard to Create Process Servers
- Configuring Platform Agents on Windows
- Configuring Load Balancing on Platform Agents
- Automatically Updating Platform Agents
- Securing Communications for Platform Agents and System Tools
- Creating a Monitoring Platform Agent
- Monitoring External Systems with Platform Agents
- Creating a Monitor Check
- Reversing Network Connections to Platform Agents
- Platform Agent Registry Entries
onsiteTopic
